14) which of the following are breach prevention best practices
Best Practices in Breach Prevention - Minimizing the Risk of a Breach. However recent studies show that protecting patient information is one of the biggest challenges that modern health practices face.
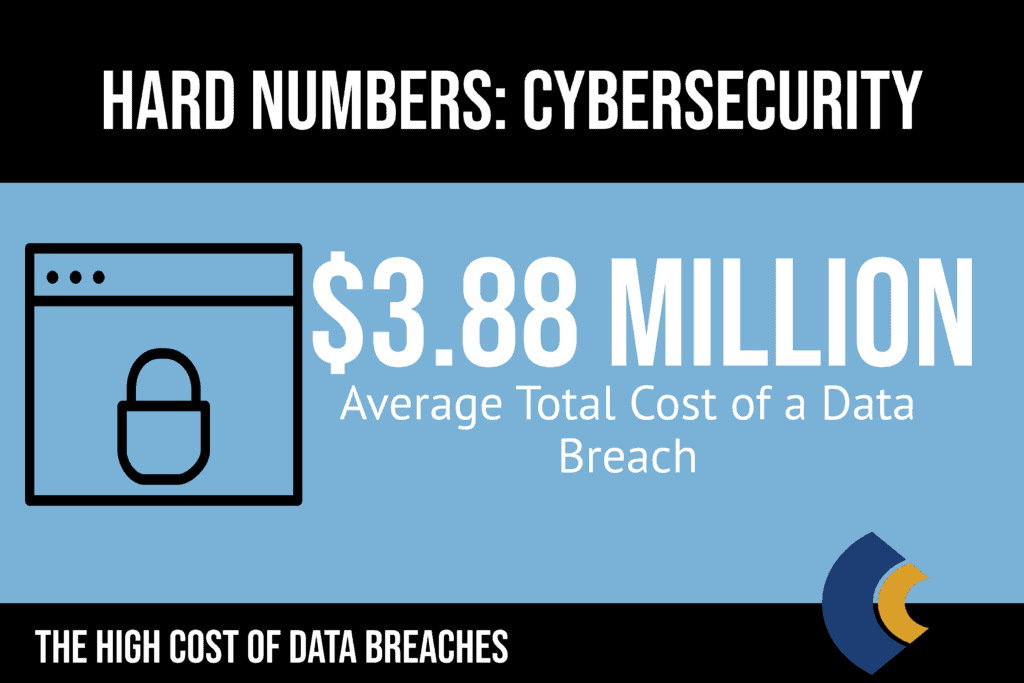
Essential Guide To Higher Education Data Breaches
When a data breach occurs involving a cloud service the impulsive reaction is to denounce using the cloud at least for sensitive information.

. Now with the GDPR in full effect we will likely see these costs increase. Implement additional security protocols. Regularly monitor networks and databases for unusual traffic.
Data breaches are an everyday reality in a connected business world. Those demands alone are enough to strain resources to the breaking point. S3 Breach Prevention.
247 help from Expert Tutors on 140 subjects. An individuals first and last name and the medical diagnosis in a physicians progress report correct Individually identifiable health information IIHI in employment records held by a covered entity CE in its role as an employer. He recommends campuses have firewalls.
Since cloud security is not widely understood it may be difficult to delineate it in the context of more general information security. Addresses three types of safeguards - administrative technical and physical. Require specific authorization and credentials to access sensitive information.
Department of Justice and elsewhere that client companies should consider to be fully prepared for the realities of a cyber-based attack. Access to over 100 million course-specific study resources. You should always logoff or lock your workstation when it is unattended for any length of time.
You might also consider the following recommendations. In the United States the average total cost of a data breach stands at 819 million more than twice the global average. Which of the following are breach prevention best practices.
These 15 best practices can be used to reduce the likelihood of a data breach and help you respond more quickly to an attack. Full access to over 1 million Textbook Solutions. A single technology cannot provide complete protection.
Data Breach Response Guide at p. Compliance required by 92314 New BAAs executedrenewed after 12513 Must conform to new rules. All of the above answer a.
Breach Notification Rule - 45 CFR 164400-414 If an impermissible use of disclosure of PHI is determined to be a Breach CEs must provide notification of the Breach to affected individuals the Secretary of HHS The Secretary state entities under applicable state law and in certain circumstances to the media Reputation. This was a result of 2935 data breaches. Attracting new customers or regaining the loyalty of existing customers following a successful and widely publicized breach is very difficult task.
Which of the following are breach prevention best practices. Perform suspicious email training exercises to help employees identify potentially nefarious emails. A Summary of Cybersecurity Best Practices at p.
Train employees on data security practices and awareness. PCs cell phones PDAs and the network says Pappas. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business associate BA b.
Invest in up-to-date data loss prevention DLP technology. Ensure that software and hardware remain up-to-date. Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security.
Best Practices for Enterprise Cloud Security. Following this sheet is the Summary and Next Steps sheet a. Read this best practices guide.
Sensitive data about identity collected stored transmitted or processed. IIHI of persons deceased more than 50. Protects electronic PHI ePHI c.
They need to be secure at the host eg. What is the best. See Page 1.
While cybersecurity threats are impossible to completely eliminate taking some necessary precautions can significantly reduce risk and help to prevent data breaches. Attorneys should promote the following five best practices as gleaned from the US. Results of an eye exam taken at the DMV as part of a driving test.
There are Microsoft best practices best practices and practices. Organizational leaders know this. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary andby promptly retrieving documents containing PHIPII from the printer.

6 Steps To Developing A Data Breach Response Plan Spectral

Board Oversight Of Cyber Risks And Cybersecurity Imd Article

Orca Security Launches Industry S First Cloud Risk Encyclopedia To Provide Ongoing Education For Cloud Security Best Practices Business Wire

Enterprise Data Breach Causes Challenges Prevention And Future Directions Cheng 2017 Wires Data Mining And Knowledge Discovery Wiley Online Library

How To Prevent Data Breaches 12 Best Practices Paysimple
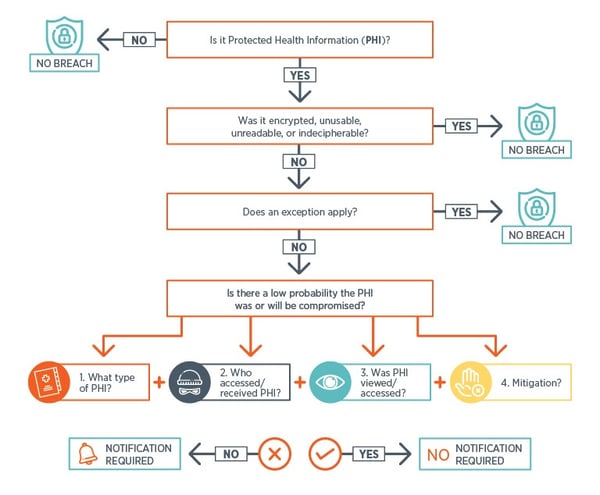
Preventing Hipaa Data Breaches Case Studies And Best Practices

How To Prevent Data Breaches In 2022 Upguard

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System

Preventing Hipaa Data Breaches Case Studies And Best Practices

6 Most Common Causes Of Data Leaks In 2022 Upguard

Recent Cyber Attacks Data Breaches In 2021

Analyzing Company Reputation After A Data Breach

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System

Which Of The Following Are Breach Prevention Best Practices Public Health

What Is A Man In The Middle Attack Mitm Attack Prevention

6 Most Common Causes Of Data Leaks In 2022 Upguard
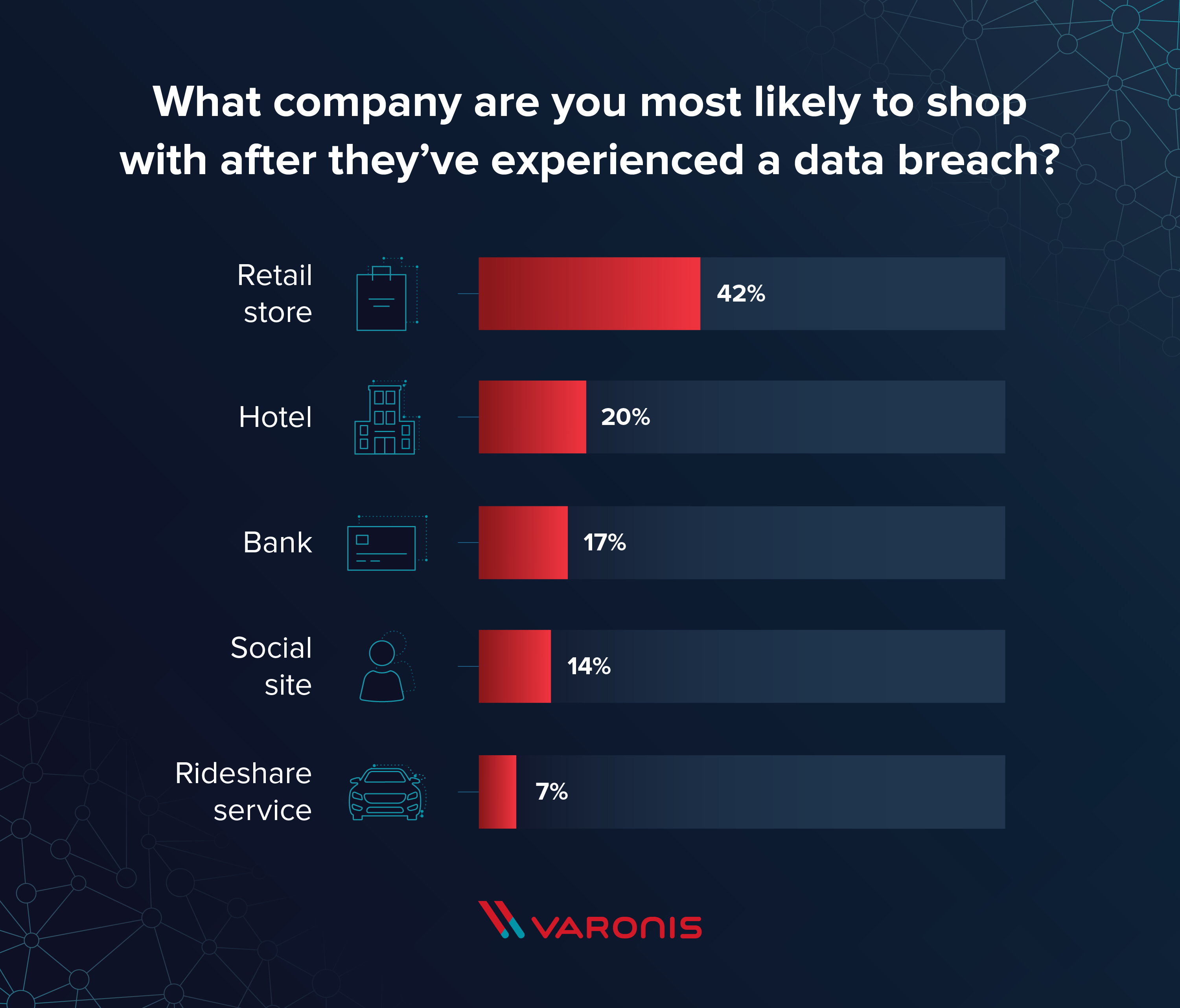
Analyzing Company Reputation After A Data Breach
5 Best Practices For Data Breach Prevention Endpoint Protector
